Cybercriminals Target Disgruntled Employees to Deploy Ransomware
How do businesses protect themselves?
(Louisville Geek | August 27, 2021) -- Picture this scenario.
William is an intelligent, up-and-coming 32-year-old IT technician. For the past three years, he’s overseen the organization’s migration to the cloud. Even though he’s passionate about IT, he’s become increasingly frustrated with the leadership. He doesn’t trust their vision for the company, plus he feels he’s underpaid and undervalued.
One day the vice president lashes out at him in front of the entire team for something that wasn’t even his fault. He decides ‘enough is enough’ and begins polishing his resume. He starts skimming job boards, updates his LinkedIn profile, and sends a few feeler messages to his network notifying them that he’s looking for a new job.
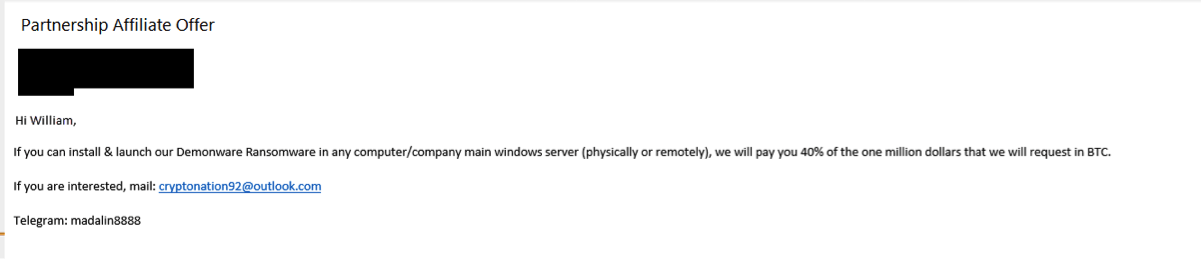
Then, out of the blue, he receives the following email message:
Translation:
William, are you interested in making some money before you leave the company? If so, all I need you to do is install a file on your company server. We will lock up their files and request a $400,000 ransomware fee. To compensate you for your efforts, we will pay you 40% of whatever we receive in BTC. Let me know if you are interested.
Real Threat
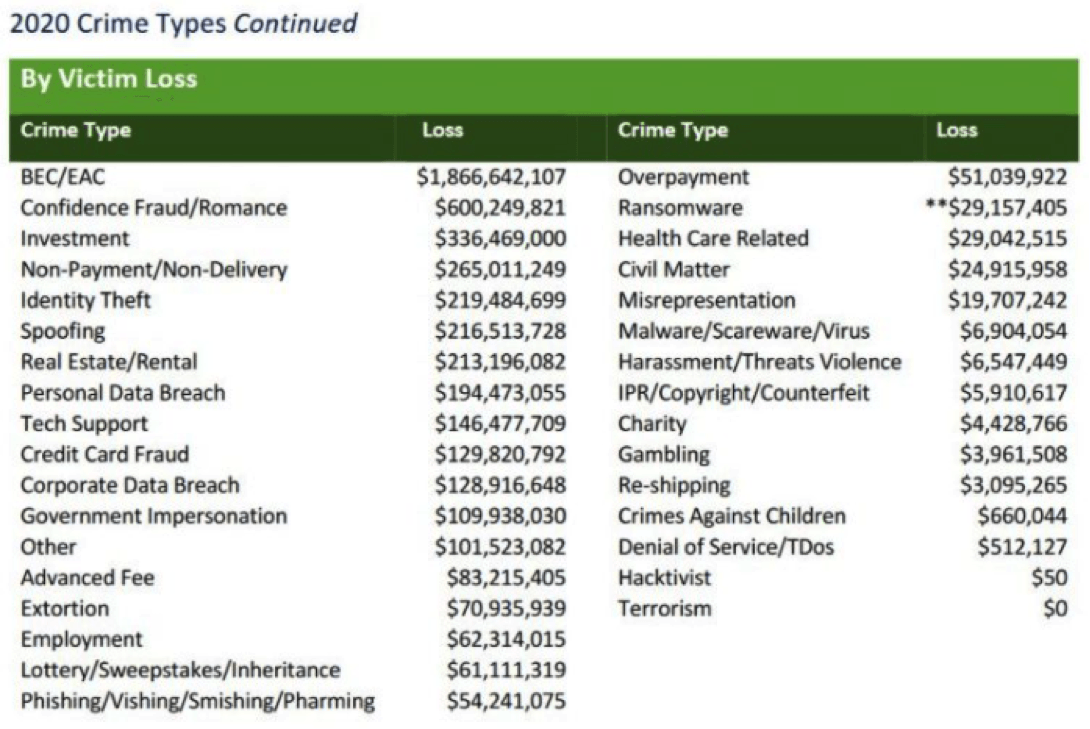
The scary thing is this: there are ransomware groups acting out this very scenario all over the globe. And, while multi-million-dollar ransomware payments are dominating the headlines, the biggest financial losses tied to cybercrime each year stem from social engineering tactics just like this. These are called Business Email Compromise (BEC) or CEO Scams (where cybercriminals impersonate the organization’s CEO), and according to the latest figures released by the FBI, the reported loss from these threats increased to $1.86 billion in 2020.
- Ensure two-factor authentication is applied on all apps, tools, and logins.
- Educate your employees about the latest cybersecurity trends and threats and to be mindful about what they post on their own social media accounts.
- Inform your employees about the responsible use of social media. Let them know that this is not only for the organization’s sake, but for theirs as well.
- Ensure that your organization has an offboarding plan that revokes access to any employee leaving the company.
More FEI Louisville News